TECHNOLOGIES
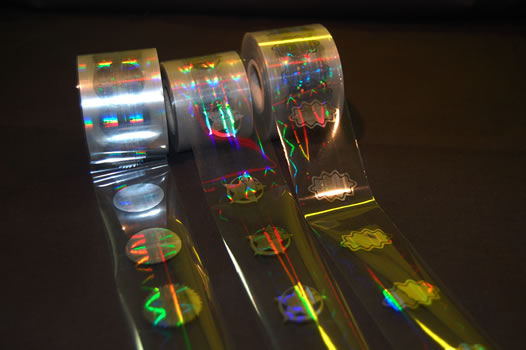
The hologram is the 3D recording of a graph. Nowadays, the hologram is the most used system for reducing the risk of forgery, proving tampering and protecting a brand. That is because the hologram is generated by a technology that prevents it from being reproduced by a scanner or photocopier so that the security and quality can be guaranteed and enhanced by adding various holographic techniques, such as:
-
2D/3D
2D graphs with different depth levels (3D).

-
Zoom Effect
By inclining the hologram, the image increases or decreases its size.

-
Microwords
Micro and nano texts, which are only visible by means of a magnifying glass or a microscope.

-
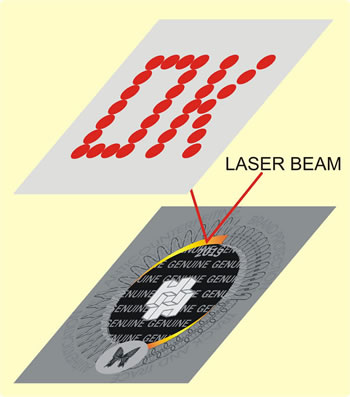
• Hidden images
The image is displayed by a laser beam on an opacified screen.
-
Truecolor Effect
The image can be seen from a specific angle with natural colors.

-
Kinetic Holographic White Effect
Kinetic effect made up of different grey levels (non-diffractive).

-
Flip effect (2 channels)
Two diffractive superimposed images alternatively appear when the visualization corner of the hologram is changed.

-
Guilloche Effect
A number of thin diffractive lines forming a complex geometric figure.

In addition, other security systems are used, such as:
-
Track code managed also via the Internet
Sequential number, alphanumerical random codes, random, barcode, data matrixes and QR codes.

-
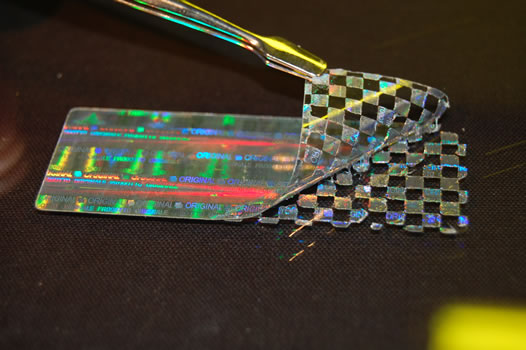
Tamper Evident materials
Materials made through a metallization process that make tampering attempts evident by fragmenting the holographic image.
-
UV and IR markers
Inks allowing the visualization of texts and images by means of an ultraviolet or infrared light.

-
Security inks that can be customized
-
Laser ablation
Selective removal of metal for writing permanent variable data on the holographic seal.

-
Demetallization
Selective removal of metal to create guilloche, pattern and high resolution images.